A Brief History
Conficker is a new and interesting breed of self updating computer worm. It is also known as Downup, Downadup and Kido. It was discovered in October 2008. It exploits a known security problem in Microsoft Windows Operating System. The operating systems vulnerable includes Windows 2000, Windows XP, Windows Vista, Windows Server 2003, Windows Server 2008, and the Windows 7 Beta. The havoc created by this worm can be guaged from the fact that Microsoft has placed a bounty of $250,000 for the person who wrote it. The various versions of Conficker has infected an estimated number of more than 10 million IPs.
Types of Conficker Worms
Currently three types of the Conficker worm havfe been detected:
Conficker A
Conficker B
Conficker C
Precautions
1. Get the MS08-067 update if you have not done it already.
2. Disable autorun. To disable autorun follow the following steps:
* Open notepad and copy the following code:
REGEDIT4
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\IniFileMapping \Autorun.inf]
@="@SYS:DoesNotExist"
* Save the file as “autorun.reg”.
- Navigate to the file location and double click on it.
- Delete the following registry key:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2
Symptoms
Conficker A:
*Creation of random files in %Sysdir% folder.
- Sometimes creation of the following files have also been observed:
-%Program Files%\Internet Explorer\[Random].dll
-%Program Files%\Movie Maker\[Random].dll
-%All Users Application Data%\[Random].dll
-Temp%\[Random].dll
-%System%\[Random].tmp
-%Temp%\[Random].tmp
*Creation of random services by modifying the following registry keys:
-HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\{random}\Parameters\”ServiceDll” = “Path to worm”
-HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\{random}\”ImagePath” = %SystemRoot %\system32\svchost.exe -k netsvcs
* Creation of SMB(Server Message Block) session in port 445
- Attempts to access the following websites:
-hxxp://www.getmyip.org
-hxxp://getmyip.co.uk
-hxxp://checkip.dyndns.org
-hxxp://whatsmyipaddress.com
* Access to security related websited blocked.
- Creation of scheduled tasks.
- As with most virus infections, a significant slowdown of the system.
Conficker B:
In addition to the symptoms exhibited due to Conficker A, Conficker B infection may reasult in the following additional behaviours:
* Creation of autorun.inf files in removable storages.
- Access to admin shares denied
Conficker C:
Conficker C is very new and its behaviours are not known properly.
Removal
Here we will describe a method to remove Conficker manually. However we do not advice manual removal as the first choice.
1. Login as a local user. Avoid logging in with a Domain Account.
2. Stop the Server Service and Task Scheduler Service.
* To disable any service follow the following steps:
– Goto start->Run
– Type in “msconfig” and click ok.
– The “System Configuration Utility Window” will come up.
– Goto the tab “Services” and uncheck “Server” and
“Task Scheduler” from the services list.
– Click “Ok“.
– Restart the system and login as a local user again.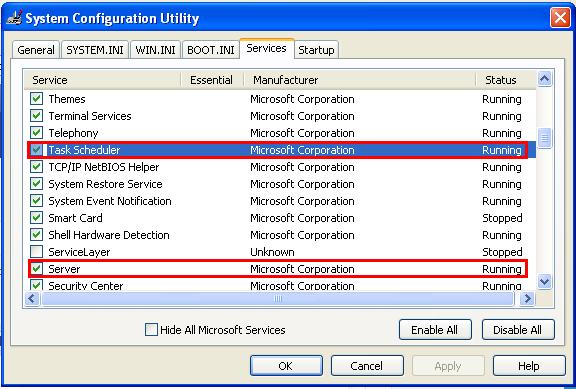
3. Download MS08-067 and manually install it.
4. Goto start->Run. Type in “regedit“.
* In the registry editor window that open, locate HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SvcHost.
- On the right pane locate “netsvcs” and double click on it.

- A list of service names will come up.
- Find any random looking entries,note the names and delete them.
- Let us call these random entries %malware% for reference.
- Leave a blank line after the last legitimate entry. Click “Ok“.
- Right click on SvcHost in the left pane.
- Click on “Permissions…” and click on “Advanced” in the “Permisions for SvcHost” window.

- In the “Advanced Security Settings for SvcHost“, click on “Add“.
- The “Select User or Group” window will open.
- Enter “Everyone“, click on “Check Names” and then “Ok“.
- The “Permissions Entry for SvcHost” window will open.
- Change “Apply onto” setting to “This key only” and check on “Deny” for “Set Value“.
- Click “Ok” wherever applicable and “Yes” at the prompt.
5. Goto HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\%malware%
* Right click on %malware%. Goto Permissions -> Advanced.
- Check the following and click “Ok“.
–Inherit from parent entries that apply to child objects..
– Replace permission entries on all child objects…
* Press f5 key to refresh.
- Now you will see “ServiceDll” on the right pane.
- Note the path given in the “Data” column for “ServiceDll” and change it to somthing else.
- Let us call the original path above %path% for reference.
- Goto HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- Check if %malware% is listed there.
- If yes, remove it.
- Repeat step 5, if you found more than one random names in step 4.
6. Disable Autorun by following the steps given in Precautions above.
7. Reboot the system.
8. Goto %path%.
* Right click on the file.
- Goto Propreties->Permissions
- Enable “Full Control” for everyone.
- Then delete the dll file.
9. Goto start->Run. And type in “AT /Delete /Yes” and run.
10. Update your system.
Note: This removal does not cover Conficker C
Sources: McAffe MSDN Blogs US-CERT
Technorati tags: Conficker Removal Precautions Detection